Security Metrics Analysis
Data extracted from the papers
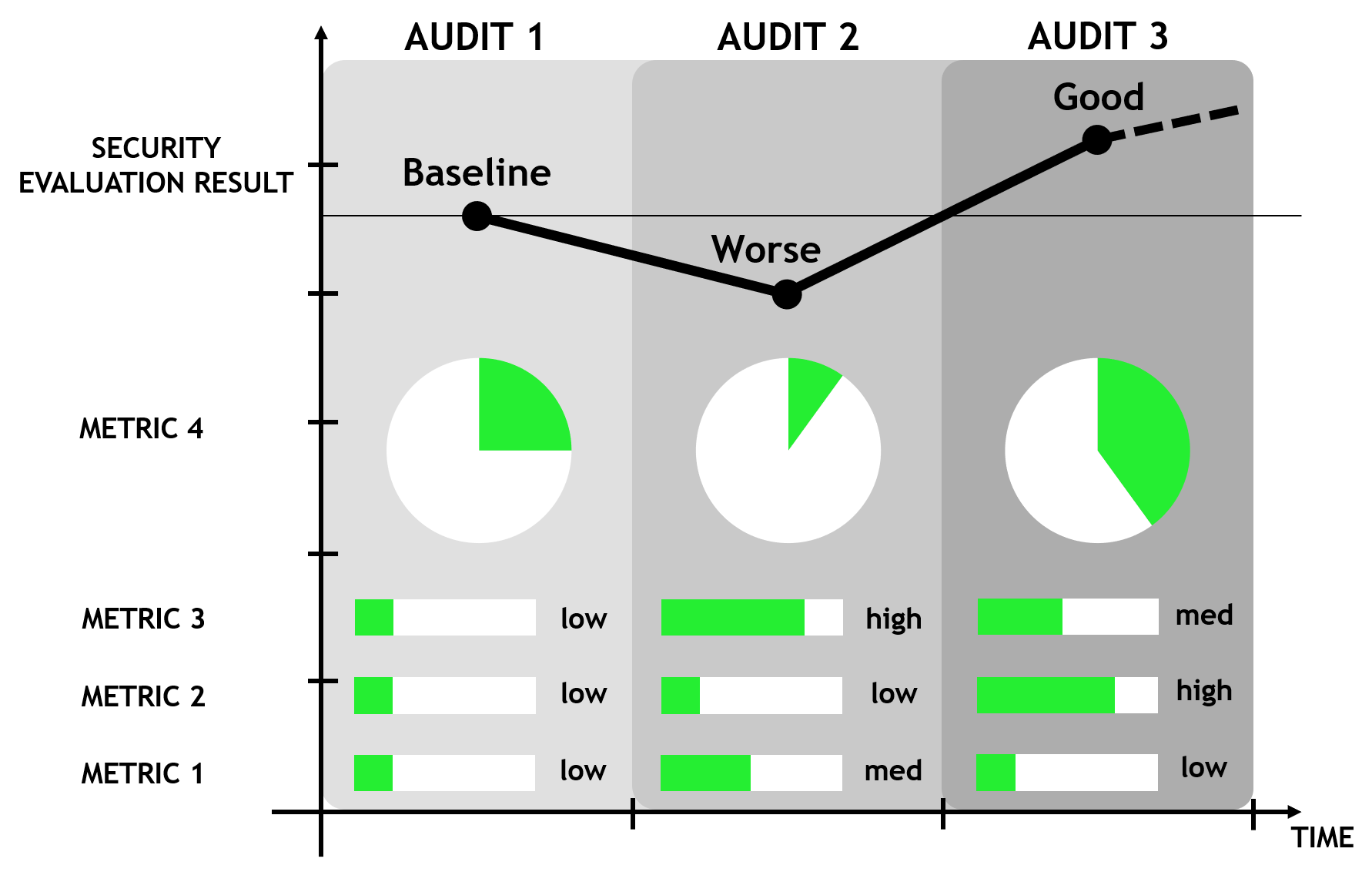
This is the data set used to carry out a systematic review of the literature to find the metrics that have been proposed so far. The data sources used were online databases, conference proceedings and academic journals of IEEE Xplore, Elsevier, AMC Digital Library, Springer, along with Google Scholar search engine. The objective is to analyze to what extent the proposed metrics can be applicable to the security evaluation of Embedded Systems.